An increasing number of applications are hosted in the cloud, and most of them are being used as software-as-a-service (SaaS). There are more and more employees work outside of the headquarters and connect back to the corporate network while directly accessing to the cloud applications at the same time. Today enterprise branches have the need to access the cloud applications; however, the traditional WAN approaches, where traffic is routed back to the corporate firewall and out to the destination, were never designed for cloud-based applications.
Given this reason, some enterprises WANs render their branch networks a direct cloud access, and thus the branches are able to directly access both private and public networks. However, this could expose enterprises to security breaches that can compromise data and result in network downtime.
Problems to be solved:
> Local internet breakout exposes branch offices to possible cyber attacks as hackers know that branch network is generally a weak point in an organization.
> Headquarters-based security approaches were never designed for today’s cloud-first world.
> Firewalls have traditionally been placed on-premises at each location, requiring physical IT presence for configuration, maintenance, and troubleshooting. However, most SMEs do not have the IT resources to deal with these growing needs at branch offices.
Solution: Integrating Cloud-based Security Solution
Q-Balancer branch gateway can be a primary firewall, adding a layer of security to your existing network, or simply playing nicely with the security solution you already have in place. Also, managing and configuring firewall in branch devices through our centralized management system (CMS) help enterprise IT reduce time for travelling and security setting.
Cloud-based security solution provides great opportunities for enterprises to reduce latency and costs, while improving their security posture at the same time. Q-Balancer branch gateway is able to work with cloud-delivered security solutions on the market, which is beneficial for organizations with limited on-site IT resources.
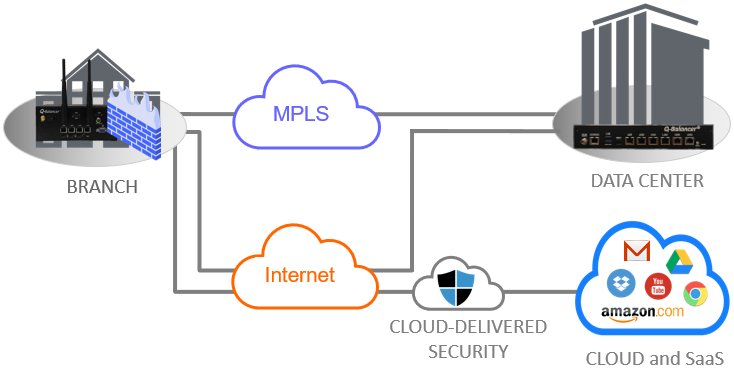
Integrated Cloud-based Security Solution
In the diagram illustrated above, a security policy may be defined, for example, below:
> Sending all internet-bound traffic directly to the cloud-delivered security vendor.
> Backhauling all other traffic to next-generation firewall based in the data center or headquarters.
























































